
Dynamic Risk Assessment and Threat Prioritization
State-of-the-art technology to identify where the problems are, how to solve them and where to begin
Fill in the form and we will call you back

Risk Assessment Objetives
Risks determine the probability of a threat materialization, and the impact it may produce on its target if it becomes a reality. Cybersecurity risk assessments will help us understand which points we have to emphasize when drawing up a security program, adding the necessary activities within a Security Master Plan, or the appropriate processes and procedures in the company's cybersecurity policy.
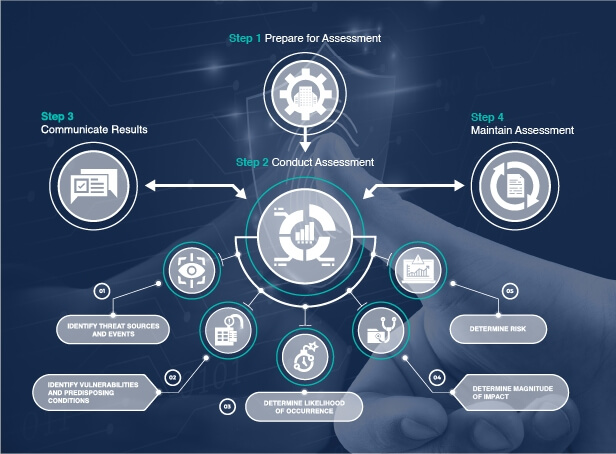
Risk Assessment Approach
Dynamic Risk Methodology adds functionalities to traditional risk assessment processes that help determine the state of risk at any given moment. In order to see how it affects technology and information, it is necessary to follow a technical approach that allows us to identify vulnerabilities, assets, and values that are associated with confidentiality, integrity and availability of information.
More information about the Dynamic Risk Methodology developed by Tarlogic can be found at Dynamic Cybersecurity Risk Assessment.
Threat Priorization
Through security reviews and penetration tests, we can identify vulnerabilities within the infrastructure and applications amongst other things.
An essential part of risk analysis is the the risk analysis framework, asset and vulnerability identification. Companies usually receive lots of information regarding vulnerabilities that are received through different suppliers and sources of information however prioritization work allows us to prioritize those vulnerabilities to show you what should be resolved with greater urgency.
You will find more information about methods to prioritize vulnerabilities in our articles at our cybersecurity blog.