Tarlogic detects a hidden feature in the mass-market ESP32 chip that could infect millions of IoT devices
• At RootedCON, the Tarlogic Innovation team presents research revealing undocumented commands in the ESP32 microchip, present in millions of smart devices with Bluetooth
• The cybersecurity company has designed a unique tool to perform security audits of Bluetooth devices on any operating system
Tarlogic Security has detected a hidden functionality that can be used as a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this hidden functionality (click here for technical details of the research) would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
This discovery is part of the ongoing research carried out by the Innovation Department of Tarlogic on the Bluetooth standard. Thus, the company has also presented at RootedCON, the world’s largest Spanish-language cybersecurity conference, BluetoothUSB, a free tool that enables the development of tests for Bluetooth security audits regardless of the operating system of the devices.
This solution, presented by Miguel Tarascó, Director of Innovation at Tarlogic, and Antonio Vázquez, a researcher in the department, seeks to democratize the execution of security tests for Bluetooth devices and help manufacturers and cybersecurity experts protect all kinds of gadgets and technological equipment from attacks that aim to spy on citizens and companies and take control of devices that are essential in our daily lives.
A €2 chip can open the door to identity theft to connect to thousands of IoT devices
Researchers from the cybersecurity company have reviewed multiple Bluetooth devices using the BSAM methodology, presented by Tarlogic a year ago, which systematizes the performance of Bluetooth security audits.
In the course of the investigation, a hidden feature was discovered in the ESP32 chip, used in millions of IoT devices and which can be purchased on the world’s most famous e-commerce sites for €2. It is this low cost that explains why it is present in the vast majority of Bluetooth IoT devices for domestic use. In 2023, the manufacturer Espressif reported in a statement that one billion units of this chip had been sold worldwide to date.
Tarlogic has detected that ESP32 chips, which allow connectivity via WiFi or Bluetooth, have hidden commands not documented by the manufacturer. These commands would allow modifying the chips arbitrarily to unlock additional functionalities, infecting these chips with malicious code, and even carrying out attacks of identity theft of devices.
In this way, malicious actors could impersonate known devices to connect to mobile phones, computers and smart devices, even if they are in offline mode. For what purpose? To obtain confidential information stored on them, to have access to personal and business conversations, and to spy on citizens and companies.
Democratizing Bluetooth device security audits
How can backdoors and vulnerabilities be detected before hostile actors exploit them? By conducting Bluetooth security audits.
There are currently thousands of tools on the market that allow manufacturers and cybersecurity experts to carry out specific tests around this global standard.
However, with the current tools, it is not possible to carry out comprehensive security audits of a Bluetooth device due to their lack of maintenance, dependence on the operating system and the fact that they require a multitude of specialized and expensive hardware. That is, in order to carry out this analysis work, a significant effort has to be made to be able to execute the tools since they do not work on a single operating system such as Windows, Mac or Linux…
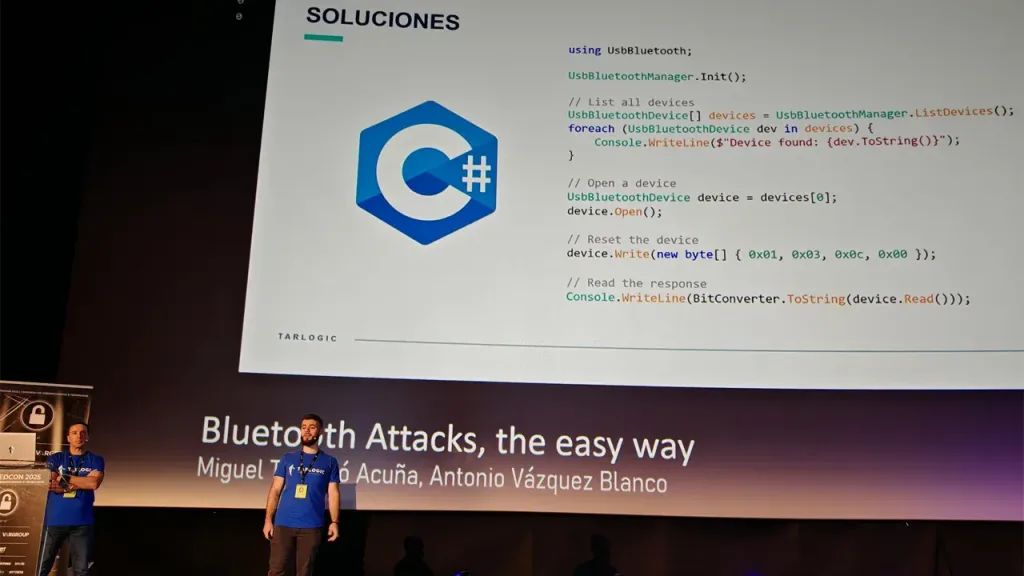
To overcome these barriers, Tarlogic’s Innovation Department has developed BluetoothUSB, a driver that allows security tests and attacks to be implemented to achieve complete security audits on all kinds of devices regardless of the operating system or programming language and without the need for a wide variety of hardware to carry out all the tests in an audit, all free of charge.
BluetoothUSB aims to facilitate development and democratize access to the tools needed to analyze the security of the Bluetooth standard in millions of IoT devices. Thanks to this software, it is possible for manufacturers to develop tools to perform their tests on all kinds of Bluetooth gadgets.
BlueTrust, BSAM and BluetoothUSB: At the forefront of Bluetooth security
The presentation of BluetoothUSB represents a new milestone in Tarlogic’s commitment to improving Bluetooth security, a global communications standard used by millions of devices using free methodologies and tools.
Thus, in 2023, BlueTrust was unveiled, a vulnerability that allows Bluetooth devices to be identified and linked to each other and can be exploited to infer personal data such as names, addresses or telephone numbers. For what purpose? To carry out attacks and fraud.
How can companies and citizens be protected against this kind of vulnerability? In 2024, Tarlogic Security presented BSAM, the first methodology for carrying out Bluetooth security audits and detecting weaknesses and vulnerabilities in devices that use this standard.
Now, it goes one step further in the task of strengthening the security of millions of gadgets. Since BluetoothUSB is a tool that allows the development of all BSAM security controls and carrying out comprehensive evaluations of gadgets without having to resort to multiple software and hardware. This means a huge saving in time, effort and investment.
Tarlogic, a leading company in Bluetooth standard security
The discovery of new attack vectors in a widely used chip such as the ESP32 and the presentation of BluetoothUSB further deepen Tarlogic’s commitment to the security of Bluetooth technology.
The projects developed in recent years by Tarlogic’s Innovation team have focused on the need to strengthen the security of a standard used by millions of devices in businesses and homes around the world.
In addition, the company’s researchers have worked together with IoT device manufacturers to optimize vulnerability detection and implement more robust security mechanisms.
The presentation of BluetoothUSB consolidates Tarlogic Security as a global benchmark in Bluetooth security after several years of continuous work.
Since its foundation over a decade ago, Tarlogic Security has become a cutting-edge cybersecurity company that combines innovation and talent to provide a wide range of services in cybersecurity, cyber intelligence and defensive and offensive service auditing to numerous listed companies and multinationals.
09/03/2025 Update:
We would like to clarify that it is more appropriate to refer to the presence of proprietary HCI commands—which allow operations such as reading and modifying memory in the ESP32 controller—as a “hidden feature” rather than a “backdoor.”
The use of these commands could facilitate supply chain attacks, the concealment of backdoors in the chipset, or the execution of more sophisticated attacks. Over the coming weeks, we will publish further technical details on this matter.
10/03/2025 Update:
Technical details and content of the Bluetooth hacking talk published in the blog article.
20/03/2025 Update:
View article ESP32 hidden HCI vendor commands, technical details and use cases
