Managed Detection and Response (MDR) Solutions
Keeping your infrastructure safe from cybercriminals is critical to your business. With our Managed Detection and Response (MDR) we protect your company by preventing threats from causing a security incident or by responding to cyber-attacks helping your business return to a normal situation.
Fill in the form and we will call you back

What is MDR service?
Managed Detection and Response (MDR) is a 24x7 cybersecurity service designed to help organizations detect, contain and eradicate threats as well as recover from cyber-attacks.
MDR combines advanced technology with human expertise to provide comprehensive, round-the-clock protection against evolving cyber threats.
Features of Managed Detection and Response solutions
The MDR service relies on two main components: Threat Hunting to prevent incidents from happening and Incident Response to manage an incident already occurred
Threat Hunting
- Our Threat Hunting Team detects and contains threats as soon as they interact with your company, preventing them from causing a security incident
Main features of the MDR service
1. 24x7 monitoring to respond immediately Any alert is attended immediately (less than 2 minutes in average), initiating an investigation to confirm risks or false positives. If a response is required the detected threat is isolated with the proper authorization from business.
2. Proactive approach to detect evasive threats The service proactively looks for an increasing number of detection opportunities (Threat Hunting Intelligence™) on a daily basis. In this way, malicious activity can be detected even when no alert has been triggered.
Any detected suspicious activity arises a Compromise Hypothesis, triggering an in-depth analysis to confirm or discard threats.
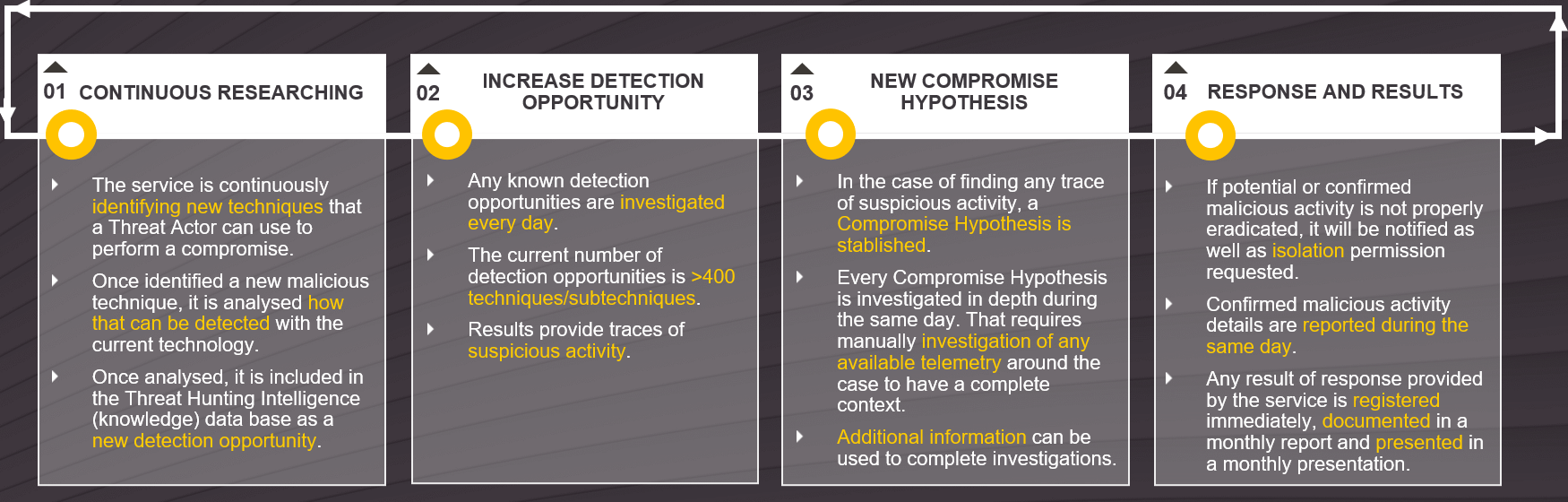
Continuous Threat Hunting approach
3. Service accelerators Among the service accelerators we can identify:
- An increasing number of detection opportunities are considered every day.

TTPs covered by our Threat Hunting Intelligence™ every day
- Continuous collaboration with our Red Team, thus allowing the identification of new detection opportunities and improve response times.

Continuous defensive capabilities improvement
4. Offensive Mindset to understand adversaries Our professionals receive offensive training to understand adversarial possibilities and be one step ahead of malicious actors.
5. Our Incident Response capabilities takes leadership in incident management including third parties or any other team that can be needed to provide the best response.

Why MDR Matters
We all are aware of organizations that are investing considerable resources in detecting advanced threats without success. Some of them are even targeted by ransomware gangs because of the lack of having good detection and response capabilities.
This scenario is becoming more and more relevant as we are learning that classic Threat Detection capabilities are not enough. We need to evolve from traditional SOC to proactive Threat Hunting. This is achieved by focusing on TTPs analysis instead of IOCs, by utilizing the Compromise Hypothesis instead of a reactive approach once a security event has been detected and more.
Threat Hunting vs Threat Detection
Traditional SOC
Threat Detection
Protects against a well-known attack.
Reactivity
The investigation stage of an alert or event.
Detection Stack
SIEM, IDS, FWs, Proxy technologies, among others.
Known attacks
Signature and IOC based detection.
Complex Start-Up
Deployment of technology, creation of use cases, source diversity, blind spots, configuration faults, alerts and false positives.
Advanced approach
Threat Hunting
New forms of attack are being investigated.
Proactivity
We are constantly investigating under an undetected breach scenario, assuming that a sophisticated attack has been produced and no security event has been triggered.
Telemetry & Deception
We collect and analyze activity from endpoints, servers and deception campaigns.
Targeted and Unknown Attacks
TPP, intelligence, tracking and hypothesis-based detection.
Easy Set-Up
Detección basada en la telemetría proporcionada por tecnología EDR/XDR
Incident Response
In order to be as much prepared as possible to face an incident, our service suggests a proactive preparation prior to the incident. The following models can be provided depending on the incident circumstances:
Response with Prior Preparation
- Under an annual service mode, with the Incident Response team on retainer to minimize response times.
- Agile effectiveness, with maximum guarantees of identification and containment of the incident.
- Priority response 24x7x365, with a commitment to respond in less than 1 hour.
Response without Prior Preparation
- Service on demand and in an incident situation, where in the first moments of the response it will be necessary to properly enroll the Incident Response team.
- The start of the investigations is not as immediate as in the proactive approach.
- The response will still be 24x7x365, but without a dedicated retainer.
Benefits of MDR solutions
Out there, it can be found different MDR services, considering a wide range of approaches, including the following alternatives:
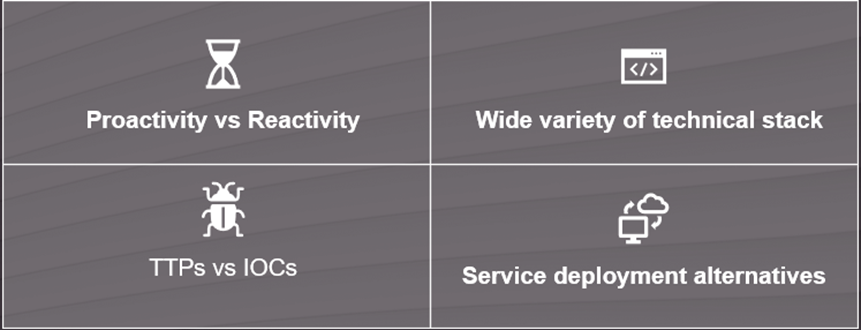
Nevertheless, our MDR model is based on:
- Proactivity to detect malicious operations even when no alert has been generated
- Approved EDR/XDR technology is critical to deliver a world-class service
- Since looking for IOCs can be easily bypassed by malicious actors, we focus on TTP enabling us to detect not only well-known attacks but also new attacks where no IOCs are available.
- The MDR deployment is usually performed during the first week of service
Why Choose Tarlogic as Your MDR Service Provider?
Our MDR service contains accelerators that make us to evolve as quick as malicious actors do. That is not only possible because the continuous improvement cycle with our Red Team capabilities, but also because our continuous researching model to include in our service the last and most advanced techniques a malicious actor can use:
Our MDR service improved not only by continuous research on Malicious Operations, Threat Actors profiling or public advisories analysis, but also by improving detection capabilities when the threat is able to perform detection bypass techniques.
All those improvements are centralized in our Threat Hunting Intelligence™ and included in our unique Threat Hunting service.
Under this context, it is particularly relevant that our Red Team is an excellent accelerator to improve our Threat Hunting solutions, and vice versa. In fact, having both solutions at the same time is a possibility that more and more clients are requesting
MDR Services FAQs
What is MDR?
MDR is a service aimed to proactively detect advanced threats in corporate endpoints and networks by using compromise hypothesis approaches, as well as responding to any potencial incident.
Who needs MDR services?
Organizations of all sizes can benefit from MDR services, particularly those without in-house Security Operations Centers (SOCs) or sufficient resources for continuous threat monitoring and response. MDR is also valuable for companies aiming to improve their security posture and address advanced, persistent threats effectively.
What are the benefits of MDR?
MDR is strongly suggested to detect and respond in front to unknown threats. That can be accomplished because instead of focusing on Indicators of Compromise (IOC), Threat Hunting focuses on Mitre Tactics, Techniques, and Procedures (TTP) to detect Malicious Operations that could perform an APT when no IOC’s are available in advance.
How does MDR improve incident response?
Our MDR service increases dramatically the response capabilities in case of incident, not only by isolating compromised systems but also assessing the impact and coordinating other teams involved in case of incident.
What technologies are commonly used in MDR?
MDR relies on advanced tools like Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR). Additionally, the service can deploy and use forensic tools in case of needed.

