Cybersecurity experts
The digital universe is full of threats. As cybersecurity experts we are here to protect your company from all kinds of cyber attacks. We analyze vulnerable points and protect you against any current or future threats.
AI Security testing services
Secure Your AI Future: Identify, Mitigate, and Innovate Safely. Comprehensive AI Security
CyberAttack Simulation
Defend your Network: CyberAttack Simulation for Proactive Security. Assess, Enhance, and Protect your Infrastructure.
Managed Detection and response
24/7 Protection: Detection and Response without Compromise. Proactive Security for a Resilient Digital Environment.
Cybersecurity services
We audit your systems and protect them
Tarlogic is one of the leading European providers of cybersecurity services. A technical team of top-level specialists and state-of-the-art solutions to provide auditing, pentesting, vulnerability management, and incident response services.
Cybersecurity services

Red Team
Realistic cyber attacks to evaluate your defenses
Our experts simulate techniques used by real-world threat actors, attacking continuously and infiltrating stealthily into your company's critical systems to identify weaknesses in defensive layers and strengthen your security.
Red Team servicesCyber intelligence
Discovering threats while supporting your business
Custom threat intelligence methodology, aligned with Tiber-EU, NIS2, and DORA standards to provide high-quality information to your business strategy. Fraud prevention with pioneering solutions against phishing and digital piracy.
Cyber intelligence services

Threat Hunting - MDR Services
A tailored solution for each company
Threat Hunting, also known as Managed Detection and Response (MDR) service, is a proactive security service. Our team of experts continuously and in real-time tracks threats to your systems, identifying suspicious activities even when no alerts are triggered. We detect and contain threats before it's too late.
Threat Hunting servicesOur Achievements
CYBERSECURITY PROFESSIONALS
CUSTOMERS PROTECTED
FLAGS CAPTURED
ASSETS AUDITED
INNOVATION PROJECTS

EUROPEAN REGIONAL DEVELOPMENT FUND
A WAY TO MAKE EUROPE
Tarlogic has participated in the ICEX-Next Export Initiation Program and has received support from ICEX through the co-financing of European FEDER funds. The purpose of this support is to contribute to the internationalization of Tarlogic.


BlackArrow
Offensive security
Adversary Simulation
Continuously creating adversary emulations (Red teaming vs Threat Hunting) to fine-tune your defenses and protect your business information.
BlackArrowOur Cybersecurity Blogs
Discover the latest articles on cybersecurity and cyberintelligence on Tarlogic's blog.
Cybersecurity blog

Critical IngressNightmare vulnerability affects the Kubernetes Ingress NGINX Controller
Information has been disclosed about IngressNightmare, a set of five new vulnerabilities affecting the Kubernetes Ingress NGINX Controller. IngressNightmare could allow a remote a[...]
Read moreBlackArrow blog

MSSQL linked servers: abusing ADSI for password retrieval
Introduction When we talk about Microsoft SQL Server linked servers, we usually think of links to another SQL Server instances. However, this is only one of the multiple available [...]
Read moreCyberintelligence blog
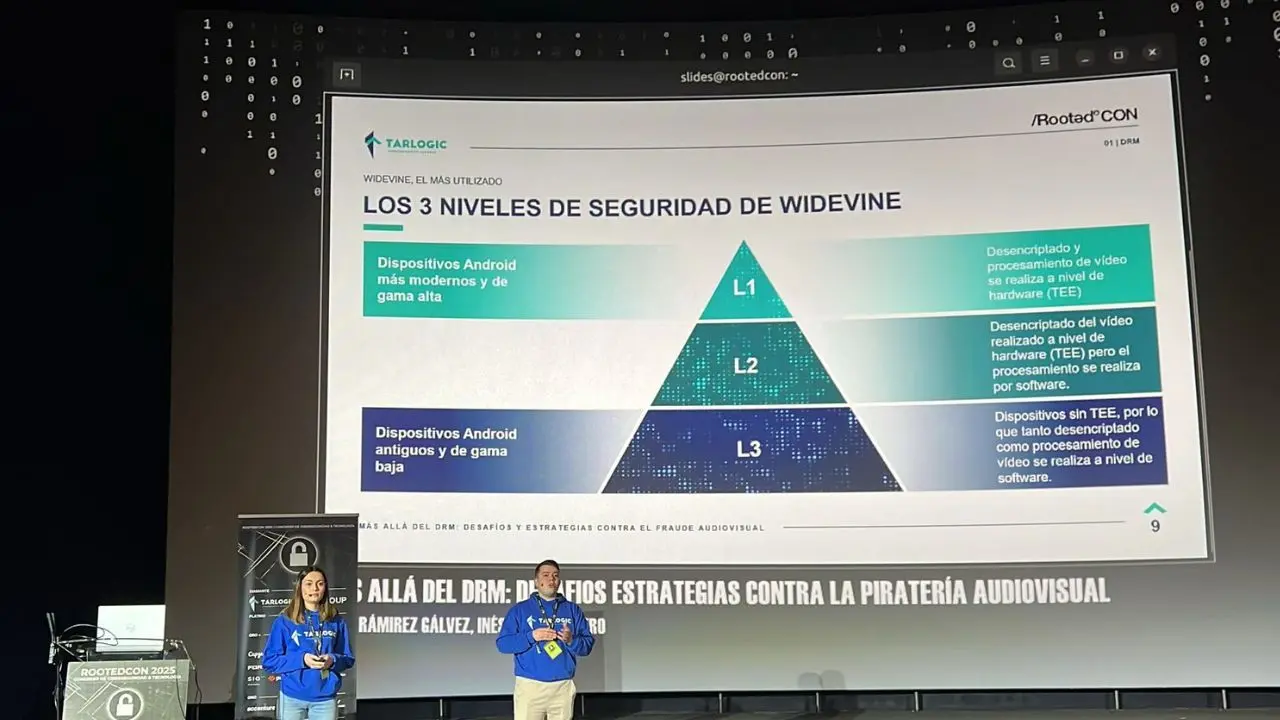
Fight against audiovisual piracy, the challenges
Combating audiovisual piracy requires continuous investigation into fraudulent activities and the optimization of mechanisms to prevent, detect and respond to them Almost one in tw[...]
Read moreCyber 4 all cybersecurity blog

Website source code audit: why is it important to do it?
By auditing the source code of a website, vulnerabilities can be detected before they are exploited and corrected in time Insecure design is one of the main security risks on a web[...]
Read more

















