Minimum encryption key size
BR/EDR
BLE
The temporary encryption keys of a Bluetooth connection can have different levels of entropy. To decide how secure a temporary encryption key for a Bluetooth connection is, the number of entropy bytes it will have is negotiated during the start of the encryption process.
Small keys, below 7 bytes, can be discovered by brute force attacks, breaching the confidentiality of communications.
Description
For verification of the minimum key size accepted by the device an encrypted connection attempt has to be made by imposing a maximum key size limitation. There is a proof of concept of the KNOB attack that allows this.
Thus, when the key entropy negotiation process is initiated, we will attempt to negotiate 1 byte of entropy to which the device must respond with its minimum key size.
In some cases, it will be necessary to make multiple connection attempts with different maximum key sizes to find out the minimum key size that allows already instead of negotiating a key size, closes the connection.
It is recommended to force the use of the maximum key size supported by the Bluetooth standard: 16 bytes.
This control will be considered satisfactory if the minimum encryption key size is at least 7 bytes.
Related resources
To check this control, the following resources can be useful:
| ID | Description |
|---|---|
| BSAM-RES-04 | Bluetooth connections sniffing |
| BSAM-RES-05 | Capture of a Bluetooth connection |
| BSAM-RES-06 | Enabling debug mode on a Bluetooth controller |
| BSAM-RES-07 | Sending and receiving HCI messages |
| BSAM-RES-09 | Changing the attributes of a controller |
Example case
The encryption key length of the pairing between a computer and Bluetooth headphones will be verified. We will use Wireshark with BTVS (btvs.exe -Mode wireshark) to capture packets for analysis. The connection is initiated through the integrated Bluetooth device management application in the operating system.
In the Wireshark capture, the pairing process is identified with a Pairing Request command, followed by the Pairing Response command, and the pairing is confirmed with the Pairing Confirm command.
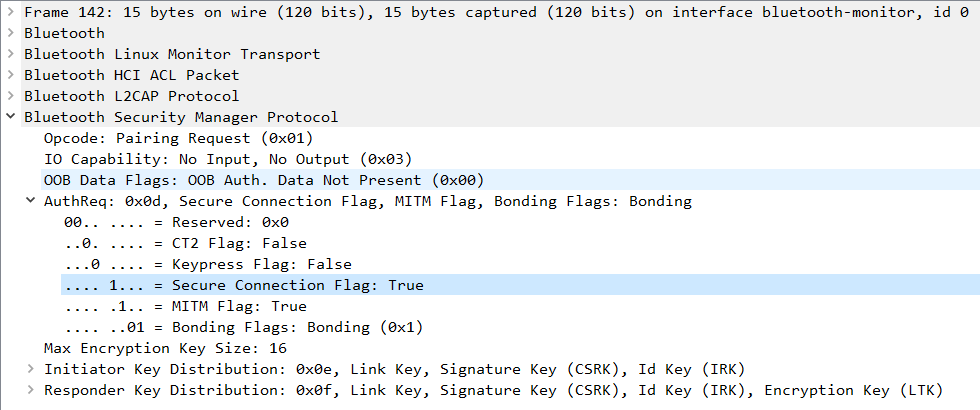
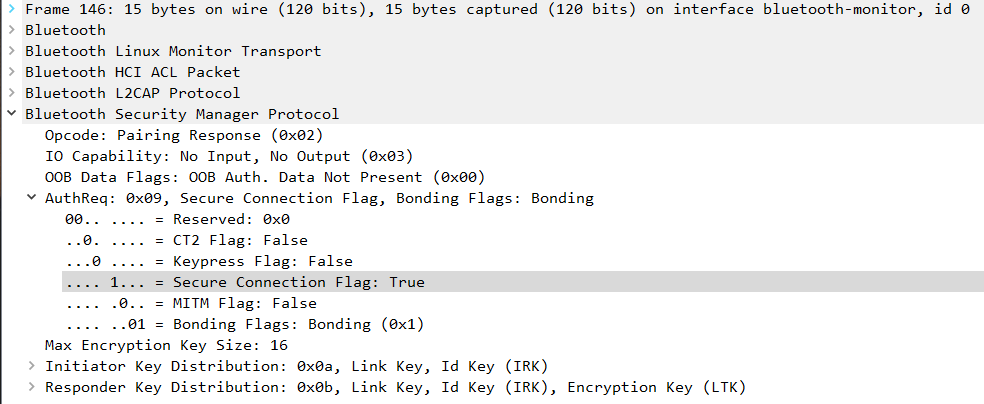
In the Pairing Request and Pairing Response commands, there is a field called Maximum Encryption Key Size, indicating the maximum length of the encryption key in bytes. This field should have a length between 7 and 16 bytes according to the Bluetooth standard.
In the Pairing Request command from the laptop, a value of 16 bytes is shared in the Maximum Encryption Key Size field.
In the Pairing Request command from the headphones, a value of 16 bytes is shared in the Maximum Encryption Key Size field.
The Pairing Request and Secure Connections commands should always have a Maximum Encryption Key Size value greater than 6 to pass the check. However, it is recommended not to use values lower than 16.
If any device requests a key length below 7, the other device participating in the pairing must cancel the connection.
The check control FAIL if either of the two devices has a Maximum Encryption Key Size field with a value lower than 7. If this happens and the connection is established between both devices, they will not pass this check.
