Sensitive data exposure
BR/EDR
BLE
Inside the advertising packets in BLE and some extended inquiry responses in BR/EDR may contain additional data added by the manufacturer.
Some of the discovery messages contain Manufacturer Specific Data that may contain sensitive information and should be analyzed carefully.
This data should be analyzed for sensitive information and verify that unnecessary data is not being exposed.
Description
By capturing the messages issued during the discovery phase, via LE beacons or in the inquiry responses in BR/EDR, data of interest can be found, such as the services the device exposes, the name or manufacturer data.
In LE beacons, manufacturer data is exposed in AdvData fields, while in BR/EDR, it is exposed in Extended Inquiry Result messages. In both cases the field is of type Manufacturer Specific Data, with id 0xFF, and a manufacturer identifier is given which can be looked up in the Bluetooth Assigned Numbers document.
The content of the Manufacturer Specific Data type is in a manufacturer-dependent format that may not be publicly available and may require a reverse engineering effort to decode.
Some popular formats for this field are the following:
Related resources
To obtain Bluetooth LE beacons or Extended Inquiry Response messages, the following resources may be useful:
| ID | Description |
|---|---|
| BSAM-RES-04 | Bluetooth connections sniffing |
| BSAM-RES-05 | Capture of a Bluetooth connection |
| BSAM-RES-08 | Device discovery |
Example case
A Samsung Galaxy Buds2 headset, during discovery, emits two different LE beacons and responds to inquiry requests with an Extended Inquiry Result message. We will use Wireshark with BTVS (btvs.exe -Mode wireshark) to capture packets for analysis.
When Wireshark is opened, the computer initiates the scanning of discoverable devices. Beacons publish device information in different formats. The first one indicates as Samsung manufacturer ID and part of the device name can be read:
![]()
The second shows a Microsoft manufacturer ID:
![]()
The Extended Inquiry Result message contains different data with the Samsung vendor ID, as well as two listings of UUIDs corresponding to the device services:
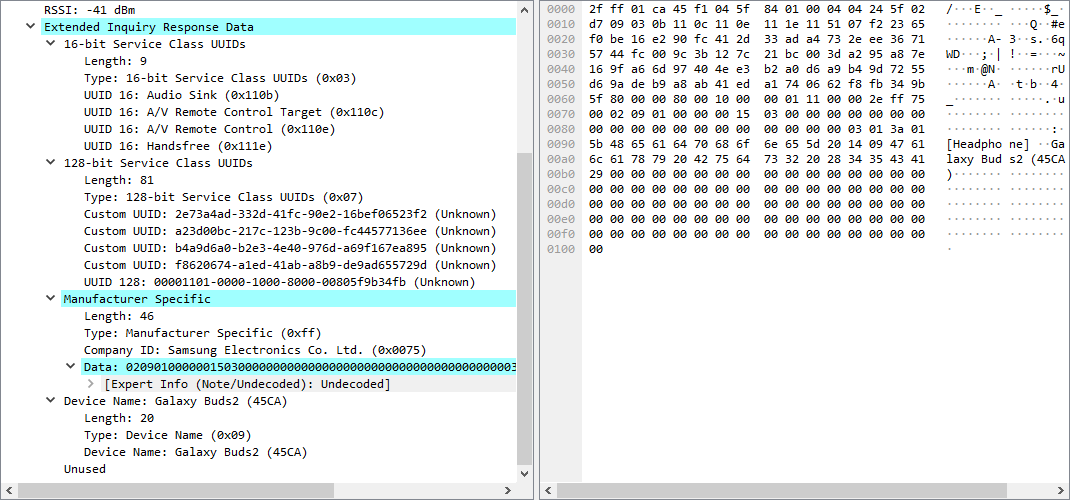
In all three cases, manufacturer data is found with unknown encoding, but shows data on the device name (Buds2) and its utility ([Headphones]).
The exposed services, on the other hand, indicate 5 services with non-standard UUIDs that expose the manufacturer’s own services. This information may be useful to the auditor in later phases of the analysis and it is preferable to avoid exposing services unnecessarily.
As this information should only be accessible in a more limited context it is interesting to highlight in the report possible solutions to this assessment. A recommendation is issued to only make the device name and services accessible during pairing mode or to another authenticated device. None of the services should be accessible to unauthenticated devices.
