The Shadow Brokers – TSB actions follow-up
Table of Contents
The Shadow Brokers are a group of hackers who made their first public appearance in the summer of 2016. Actually, this fact was quite controversial since this group had confirmed having a great number of computer hacking tools such as “exploits” or “0-day” which would enable access to almost any computer system.
The special feature of these exploits, whose property was confirmed by this group, is their origin, since they advertised that they came from US NSA. This situation pointed out that this group would have been able to access NSA computer systems obtaining not only the aforementioned exploits, but also a different kind of information.
The Shadow Brokers provided the possibility of purchasing these tools by anyone willing to pay. For this purpose the interested party would have to pay 10,000 bitcoins regardless fluctuations in currency value. Currently, the requested quantity would be higher than 25 million euros. Nevertheless, there weren’t any buyers apparently. And consequently, they delivered a part of the tools what caused a real revolution in the cybersecurity world.

It is a fact that the famous ransomware “Wannacry” in May 12th, 2017 used one of the aforementioned tools. Analyzing the success and the social, political and economic impact of Wannacry, The Shadow Brokers threatened to monthly deliver new NSA tools.
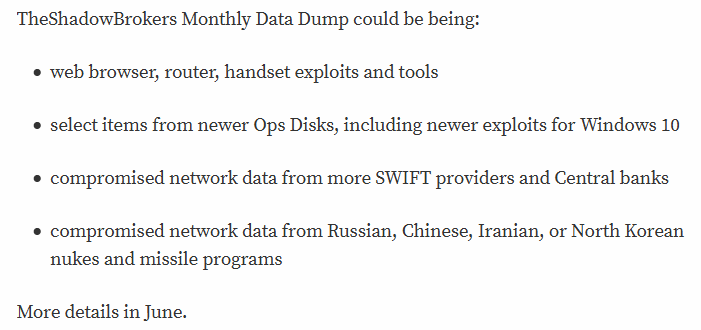
Gathering information about this group in several interventions through their official contact methods (https://steemit.com/@theshadowbrokers), the following conclusion was made: The Shadow Brokers do not list an exact set of tools. However, they name types of files or vulnerabilities that can be found:
- Banks and Swift providers compromised data
- Computer system exploits (Windows 10, included)
- Web browser, router and smartphone exploits.
- Network information extracted regarding Russian, Chinese, Iranian and North Korean nuclear missiles programs.
The Shadow Brokers sell the information
On last June 1st, The Shadow Brokers appeared again on the media offering a subscription service enabling access to the rest of the tools allegedly stolen from the NSA. For this purpose, the interested party should pay the equivalent of 35,000 euros.
According to the great success achieved in June, this group decided to offer additionally a VIP service for 140,000 euros at the time. This way, the customer would “call their attention” and therefore they would provide a preferential treatment. By the way, this service doesn’t guarantee nor specific tools transfer nor customized attacks development. It simply ensures having at least temporarily direct contact with “The Shadow Brokers” group. This might sound odd, but according to their resources, several customers had already hired this service.
It was in May, right before releasing the subscription service, when they decided to empty their Bitcoin wallet and change payment method.
The new accepted coins were Monero and ZCash. The reason explaining this change might be that both coins offer privacy and anonymity when carrying out transactions between accounts.
as.
| Service | ZCash (ZEC) | Monero (XMR) | USD-ZCash* | USD-Monero* |
| June Dump | 100 | 500 | 35.000$* | 22.500$* |
| July Dump | 200 | 1000 | 70.000$* | 45.000$* |
| August Dump | 500 | 2000 | 90.000$* | 100.000$* |
| VIP Service | 400 | – | 135.000$* | – |
| *The USD value is determined by the currency rate at the moment of purchasing the service, since due to the volatility of cryptocurrency, the value fluctuates and could be reduced up to the half in just a period of two months. | ||||
Zcash addresses, also called “T” addresses, are very similar to Bitcoin addresses. Besides, movements can be tracked. Zcash also provides “Z” addresses which are used to send and receive private funds using cryptographically protected transactions, completely anonymous and untraceable.
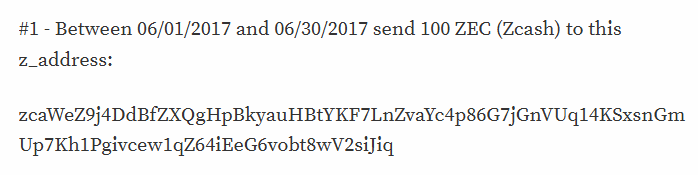
The Shadow Brokers use a data field which is sent in each transaction, where the customer is requested to add his e-mail address. This constitutes the only contact method available to be in touch with the transaction payer.
On the other hand, Monero works similarly. Different from Zcash, it adds a new field called Payment ID, an optional transaction field consisting on 32 bytes (64 hexadecimal characters).
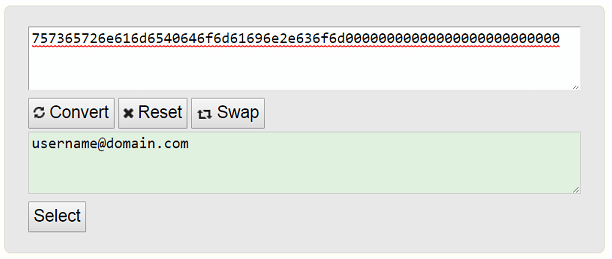
For this reason, The Shadow Brokers request encoding the email account in Hexadecimal, then complete it with zeros and finally, send it as payment ID. Considering that this is the only way the payee receives information from the payer.
The Shadow Brokers June tools leaks
As it should be, tools delivery was relatively controversial at the beginning of July. During this first week, service subscribers received the first files. One of them, fsyourmom user, published in Steemit evidence regarding the purchase and delivery receipt. In the original message, clear dissatisfaction regarding the package content was shown. The reason was that the package only contained one tool, which was a long way from achieving not even a part of the content previously promised by the group.
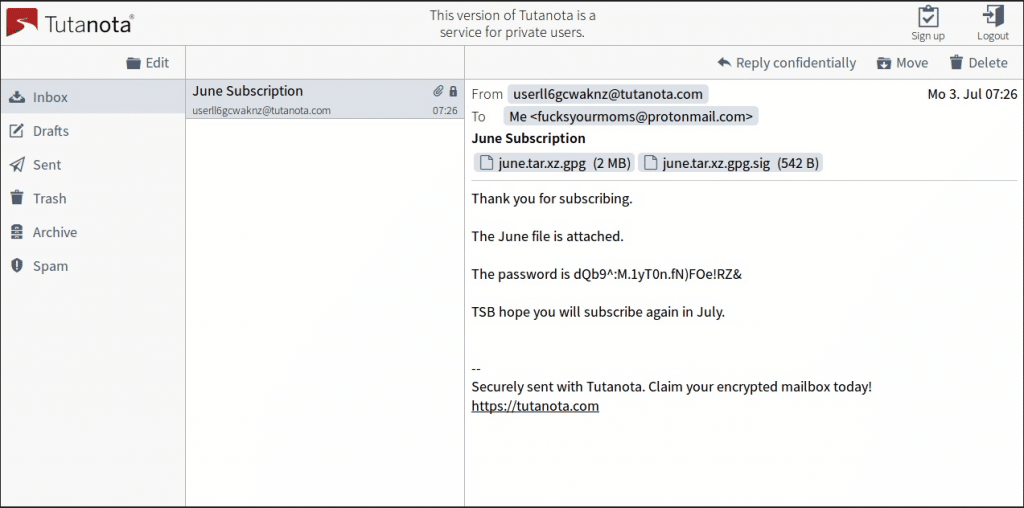
Although the real mission of this tool is unknown, this message caused that group’s credibility dropped considerably. In spite of this fact, The Shadow Brokers confirm that their campaigns were a success, and consequently they increased subscription price up to 100,000 $ in August.
With the goal of getting to know the real number of purchasers, wh1sks user (https://steemit.com/@wh1sks) examined Monero blockchain completely, analyzing each transaction and decoding the corresponding payment ID in order to make those users to carry out a transaction with the format and the amount indicated by The Shadow Brokers. This way, he obtained 3 emails, which constitutes a lower figure regarding to what was initially expected.
 This three purchasers would have sent the total amount of 60,000$ in June. This is quite far from being a “success”, taking into account that some showed publicly their dissatisfaction even providing evidence of the received files.
This three purchasers would have sent the total amount of 60,000$ in June. This is quite far from being a “success”, taking into account that some showed publicly their dissatisfaction even providing evidence of the received files.
At the moment, it is unknown what has been published in the following months or the number of purchasers that are still subscribed to this service. We hope that in the following days we know new information about subscribers and the tools sent in July in order to protect our computer systems since according to rumors new 0day are coming.
References:
https://steemit.com/shadowbrokers/@theshadowbrokers/theshadowbrokers-monthly-dump-service-june-2017
https://steemit.com/shadowbrokers/@theshadowbrokers/theshadowbrokers-monthly-dump-service-july-2017
https://steemit.com/shadowbrokers/@fsyourmoms/theshadowbrokers-are-not-making-america-great-again
https://steemit.com/shadowbrokers/@fsyourmoms/proof
Discover our work and cybersecurity services at www.tarlogic.com
