Security in PRIME networks – Current status
Since January 2019, all electricity meters for low power customers (up to 15 kW) in Spain are (or have been replaced by) smart electricity meters, allowing distributors to carry out consumption measurements and various supply point management operations remotely.
Half of the smart electricity meters in the Spanish market use a PLC communications stack based on PRIME 1.3.6 in the lower layers and DLMS in the application layer. In March 2020, Tarlogic presented the results of its research about the security of these networks at the RootedCON of the same year, demonstrating that traffic at the PRIME level was not encrypted and that, at the DLMS level, although some traffic was exchanged encrypted (using dedicated keys), most of it remained unencrypted and was authenticated by unencrypted passwords (in what is known as Low Level Security in DLMS literature).
In order to illustrate the effects that the dissemination of this information has had on the industry, Tarlogic has carried out a second, more exhaustive study which illustrates (in terms of proportion) the type of communications used, the most common access passwords and the frequency with which unencrypted data packets can be found (covering both layers). This study was carried out in two locations in Spain:
- O Barco de Valdeorras (Ourense)
- Madrid, Hortaleza district
To carry out this study it was necessary to develop the PLCTool tool, which offers a user-friendly graphical interface for security analysis of PRIME and DLMS-based networks. The tests in the town of O Barco de Valdeorras carried out in 2020 determined that:
- PRIME 1.3.6 was configured in profile 0 (not encrypted).
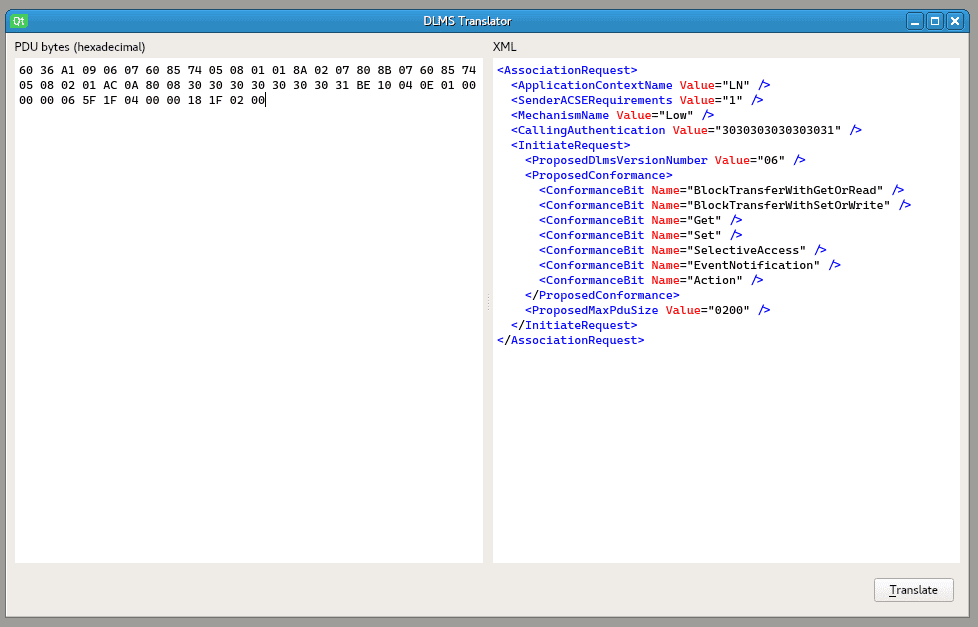
- All the authentications (AARQ) observed were carried out in Low Level Security mode, and did not negotiate any type of encryption.
- All AARQ messages used the authentication password
00000001. These credentials seemed to be used indiscriminately for reading, writing and executing methods (actions):
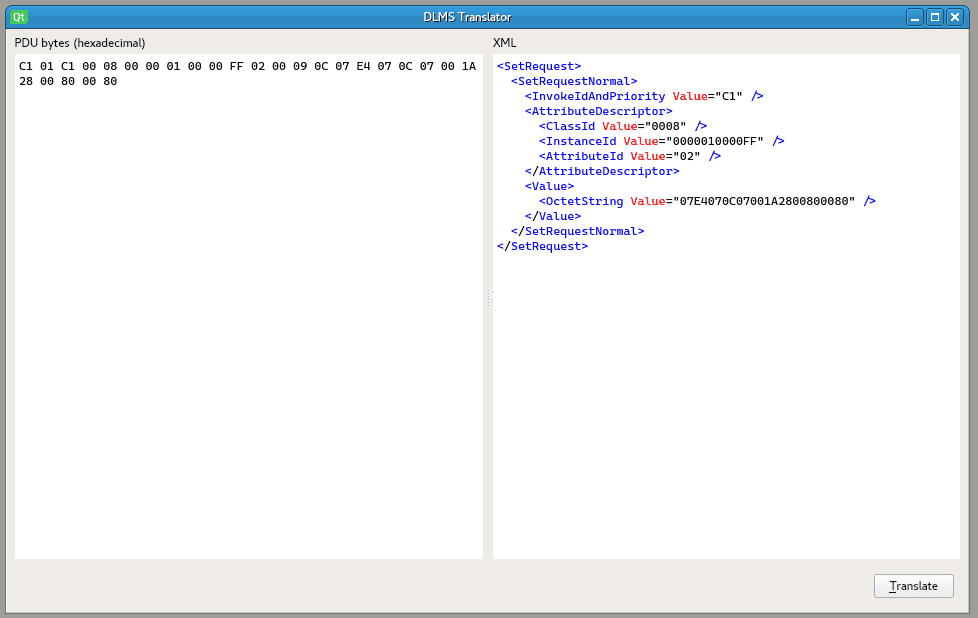
 Authentication in low security mode. Note the password 00000001 encoded in hexadecimal (303030303031).
Authentication in low security mode. Note the password 00000001 encoded in hexadecimal (303030303031).This is noted in the capture of a message of type SET_REQUEST (attribute write), against an object of class with identifier 8 (class corresponding to CLOCK type objects), setting the date and time to “2020-07-12 00:26:40” (represented in byte string as 07E4070C07001A2800800080):
Regarding the tests carried out in the Hortaleza district (Madrid) in 2020, it could be concluded that:
- PRIME 1.3.6 in profile 0 is still the standard.
- All the observed AARQ exchanges used Low Level Security.
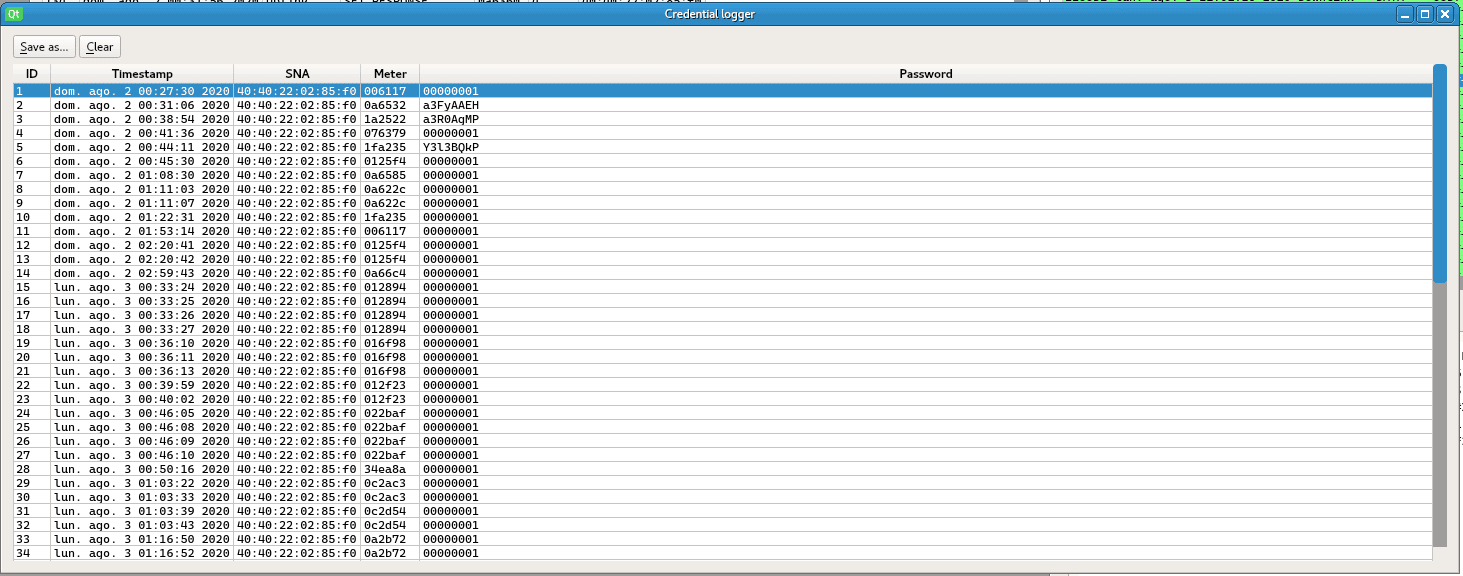
- All passwords used for reading were
00000001. - Passwords captured in Low Level Security authentication. The passwords used for writing were different for each meter:
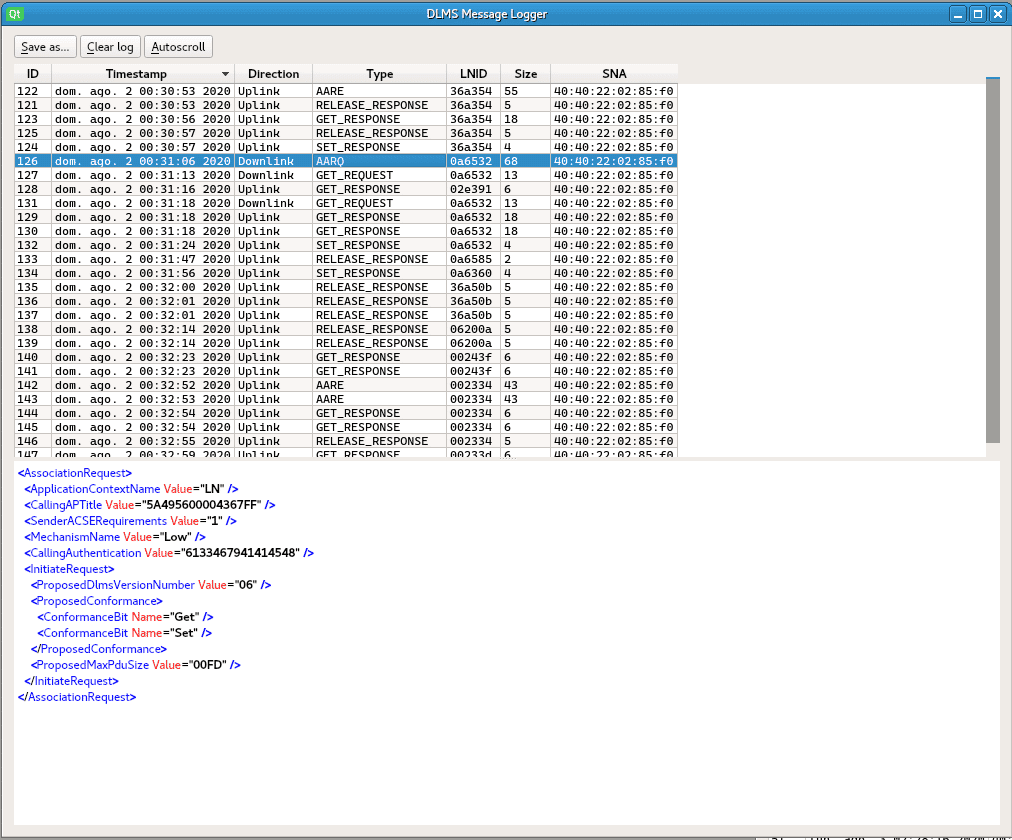
Additionally, it has been possible to observe firmware updates during the captures made. Due to the use of profile 0, exchanged information was performed without any kind of authentication:
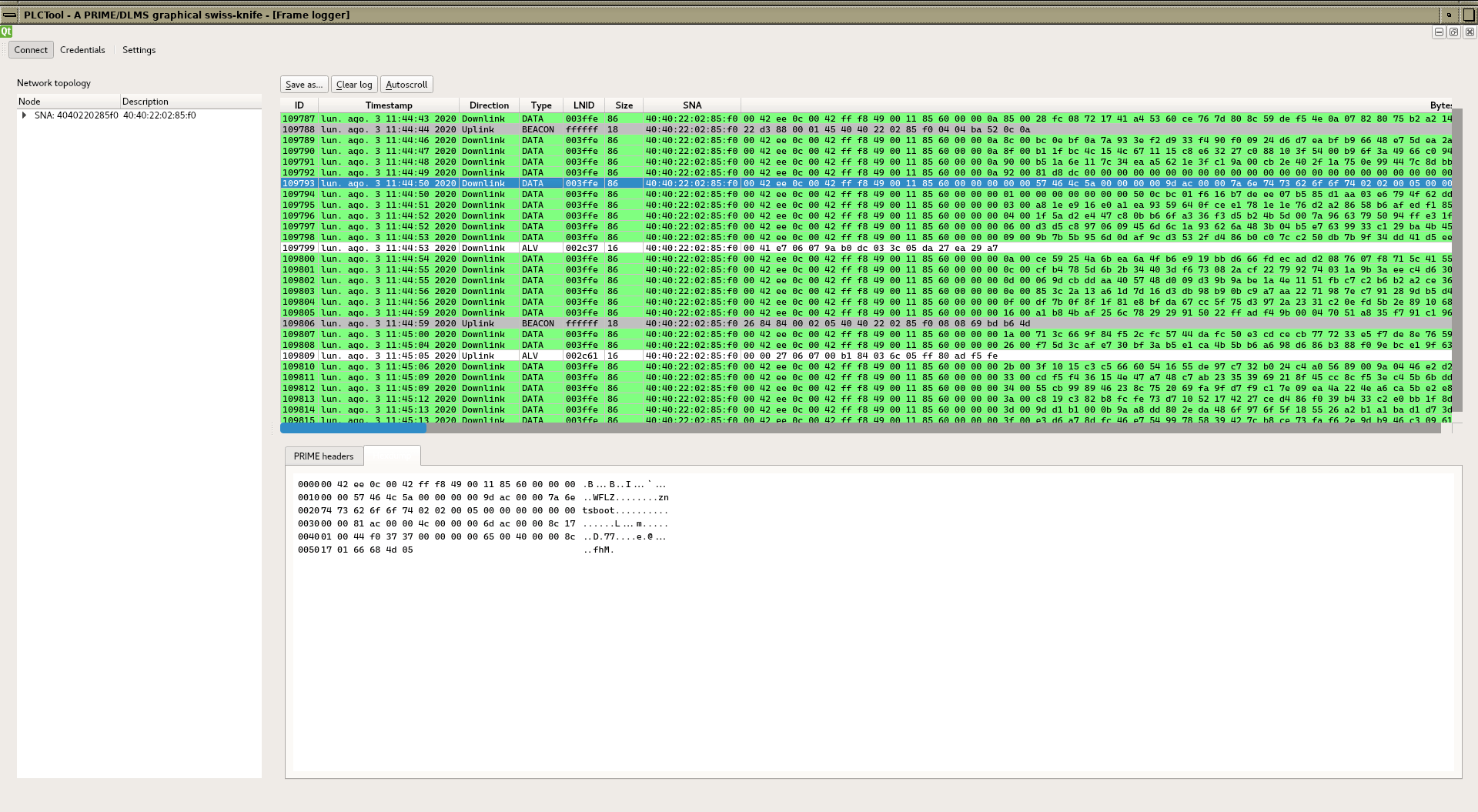 Packet containing a portion of the firmware header (the rest of the firmware was transmitted in subsequent packages). Note that, due to the unreliability of communications, the same firmware must be transmitted several times before it can be rebuilt by the destination counter.
Packet containing a portion of the firmware header (the rest of the firmware was transmitted in subsequent packages). Note that, due to the unreliability of communications, the same firmware must be transmitted several times before it can be rebuilt by the destination counter.Our conclusions are that the adoption of the PRIME 1.3.6 standard in Profile 0 is still the norm, so the PLC traffic has the following weaknesses:
- Massive use of unencrypted communications.
- Absence of authorisation mechanisms.
- Absence of authentication mechanisms.
- Absence of protection mechanisms against reinjection attacks.
- Possibility of manipulating the firmware of the counters remotely.
All of this, together with DLMS traffic in the application layer configured in Low Level Security mode (with the exchange of default unencrypted passwords) and without security at the transport level of any kind, means that the risk for these infrastructures is very high. Among the threats that are contemplated are the remote disconnection of the PCS (turning off the meter remotely), modification of the contracted power, modification of passwords and even updating of the firmware.
This information has been published in several articles on the blog [2], [3], [4] and the paper in Spanish at the RootedCON cyber security conference [5], although there are also references to previous studies such as [6] and [7].
Since the presence of Profile 0 exists in both PRIME 1.3.6 and PRIME 1.4, and as a way to push the industry to improve the security of smart meter networks and their users, Tarlogic has brought the results of this research to the attention of the industry in Spain and the PRIME Alliance. In line with good practice in security breach disclosure, they have also been informed of the intention to publish a PRIME audit tool (PLCTool) in the coming months, technical details of these attacks and how an attacker could use them to, for example, disconnect the internal PCS of a domestic meter.
The publication schedule planned by Tarlogic is as follows:
- 90 days (December 1, 2020): Release of the modem firmware + PLCTool with limited features.
- 180 days (March 1, 2021): Complete framework with working attacks.
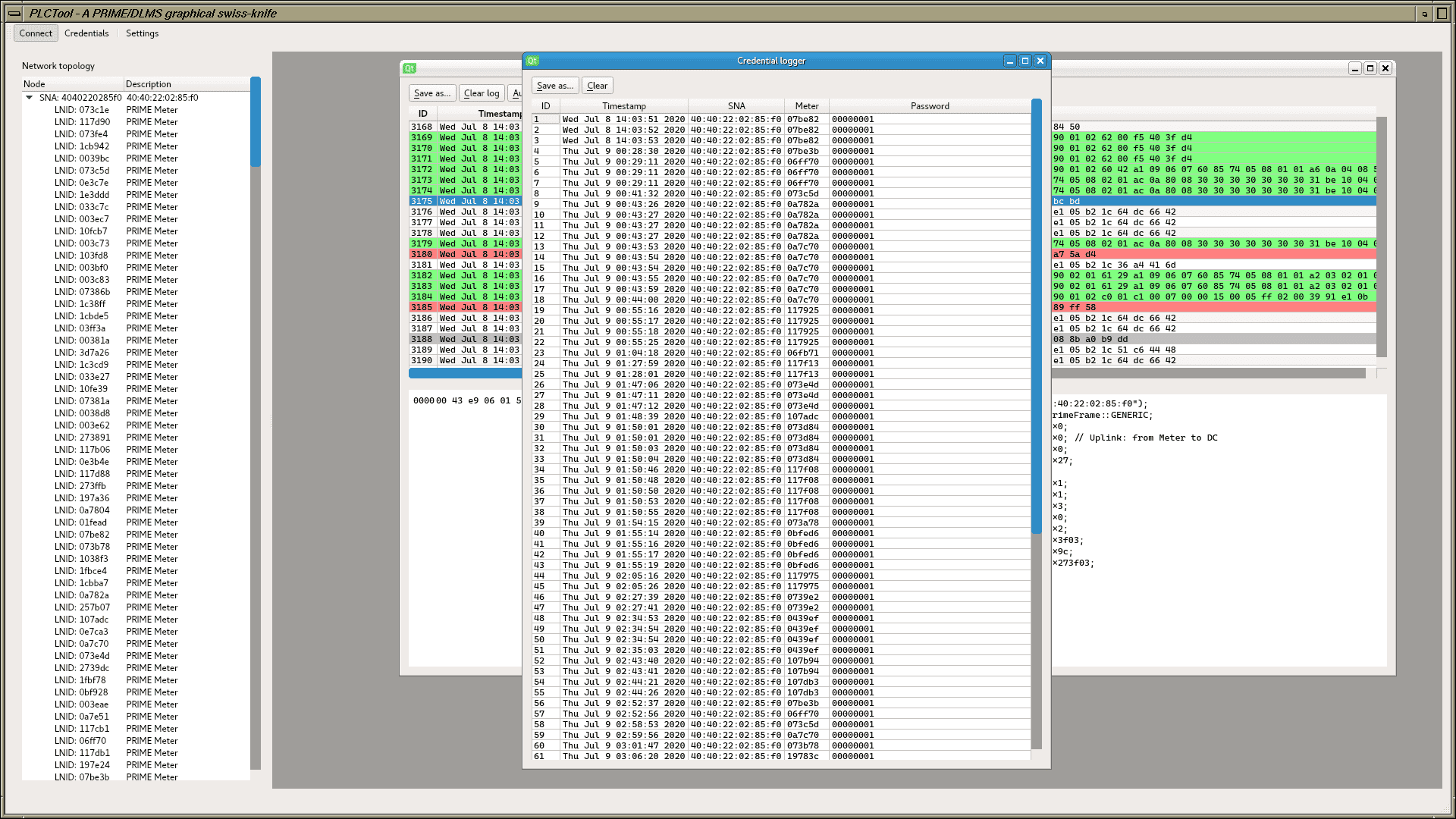 DLMS layer passwords captured after observing unencrypted traffic with profile 0 of PRIME 1.3.6 from a private individual’s home socket, using the PLCTool tool.
DLMS layer passwords captured after observing unencrypted traffic with profile 0 of PRIME 1.3.6 from a private individual’s home socket, using the PLCTool tool.References:
- RootedCon Presentationhttps://www.youtube.com/watch?v=UsVDI8oRYrA
- Seijo Simó, Miguel. López López, Gregorio. Moreno Novella, José Ignacio. “Cybersecurity Vulnerability Analysis of the PLC PRIME Standard.” Security and Communication Networks. Hindawi. 2017. https://downloads.hindawi.com/journals/scn/2017/7369684.pdf
- https://www.youtube.com/watch?v=Z_y_vjYtAWM
Discover our work and cybersecurity services at www.tarlogic.com
This article is part of a series of articles about Smart Meters
- Smart Meters – The Spanish Scenario and the Telemanagement System
- Smart Meters – Threats and Attacks to PRIME Meters
- Smart Meters – A proof of concept: hacking a smart meter
- Smart Meters – Assessing Concentrator Risk
- Security in PRIME networks – Current status
- PLCTool, the Swiss army knife of smart meters
- PLCTool plugin support