Red Team, the soldiers of the TIBER-EU program

The TIBER-EU program requires Red Team services to simulate threats to financial institutions and discover their weaknesses and vulnerabilities. The ECB wants to curb the growing number of incidents affecting banks, stock exchanges, and monetary authorities
Napoleon used to say when referring to the war that only the practice is useful. In short, it’s on the battlefield where learning the complex and ever-changing mechanisms of military discipline. Two and a half centuries later, the vision of the French general and statesman has become a kind of inspiration for the TIBER-EU program. The EU program will test the strength of the cyber defenses of financial institutions and Cyber Intelligence and Red Team services will play a key role.
The European Framework for Threat Intelligence-based Ethical Red Teaming (or TIBER-EU) driven by the European Central Bank has set out to optimize the cybersecurity structures of banks, stock exchanges, and monetary authorities.
The growing fear of a cyberattack triggering a systemic crisis has prompted monetary authorities to take action. There have been so many incidents in recent years that all the alarm bells have gone off. The recent past has acted as a catalyst for the TIBER-EU program.
What does the ECB want? It wants the banks themselves to put their defenses and vulnerabilities in check. How? Through independent providers who will require Cyber Intelligence and Red Team services to design and execute scenarios that could be triggered by an attack from adversaries.
Initially, Brussels has decided that Red Team exercises under the TIBER-EU program will be voluntary, but there is every indication that in the future they will become a practice to be followed by financial institutions, as suggested by the draft DORA in Article 23 (4) (c).
Banks have been conducting tests of this nature for some time. It’s what Jose Lancharro, the director of BlackArrow, the offensive and defensive security department of Tarlogic Security, defines as «Red Team under a TIBER scheme».
Strengthen cybersecurity structures
But all indications are that the EU program will put two more gears into the banks’ decision to strengthen their cybersecurity structures. The testing philosophy itself will go further down that road.
«The monetary authorities of each country, the Bank of Spain, for example, will validate that the attack scenarios designed are realistic. That Red Team and Cyber Intelligence services have no limitations and that, therefore, it is a realistic exercise and not one tailored to the client’s needs», argues Lancharro.
This is a very relevant issue for the future. To a large extent, if the TIBER-EU tests eventually become a mandatory practice for financial institutions, some may be tempted to approach this issue from the point of view of compliance and not as a genuine reinforcement of the institutions’ cybersecurity structures.
In other words, they may make the mistake of trying to «pass the TIBER-EU test» and not so much the quality of the content of the exercises. That is why Tarlogic Security has focused on the quality of service. In designing and executing tests that are sufficiently representative of real attacks and that cover different attack scenarios, a task for which Tarlogic considers it necessary to cover multiple scenarios over a period of approximately one year.
«That’s a broad period that can be representative of the effort that a real malicious actor can put in to attack a bank’s systems using multiple avenues. With those time frames, multiple scenarios can be covered. A single-scenario TIBER is going to be very unrepresentative of an institution’s actual resilience level», explains BlackArrow‘s director.
The TIBER-EU tests will be carried out through different phases involving different teams of professionals linked to the world of cybersecurity. After the first two articles on this community program, the first one focused on the general framework and the following one on the work of the cyber intelligence teams, the following article focuses on the work of the Red Team professionals.
A task that will be activated once the cyber intelligence services define the different threat scenarios. This information will be entered into the threat reports (GTL and TTI), from which Red Team professionals will come into play to plan and execute these scenarios.
These are, roughly speaking, the elements and steps that these teams will take to execute their part of the tests under a TIBER-EU scheme:
Tasks and objectives of a Red Team based on TIBER-EU
The Red Team, taking the above-mentioned reports as a reference, will implement several actions aimed at determining the feasibility of the proposed scenarios.
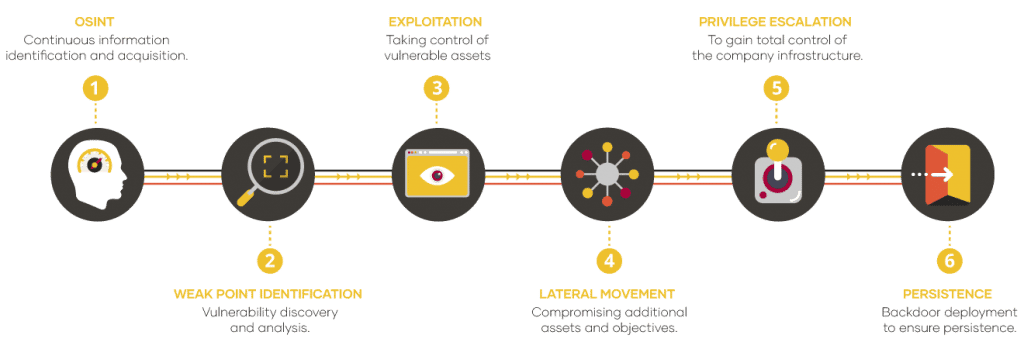
- Continuous monitoring for the location of the entity’s assets. Through this action, the different ways of penetration of key business information are made visible. For this purpose, OSINT practices are used, in a task that is carried out with the support of the cyber intelligence team
- Continuous evaluation of the possible access routes or compromise routes for both identified assets and priority business objectives. The purpose of this analysis is to assess the vulnerabilities of confidential or strategic information and critical resources.
- Verification of response and resilience capabilities in the face of attacks. Scenarios or exercises already conducted in the past are used and hostile actor TTPs are also considered following the MITRE ATT&CK classification of techniques.
- Execution of attack scenarios against the corporate infrastructure. These actions are used to identify vulnerabilities in infrastructures managed by the entity.
- Identification of security risks circumscribed to specific use cases of the client. Based on this work, the necessary improvements, both technical and executive, are subsequently proposed.
- Continuous optimization of the security governance structure. A working philosophy that allows identifying improvement actions in the short term, while preparing medium and long-term strategies.
Red Team TIBER-EU phases
The Red Team’s work is structured in three main phases: an analytical phase, a preparatory phase, and, finally, an implementation phase.
1. TTI analysis
The main objective of this phase is to know which are the critical functions (CFs) of the organization, as well as to identify the main systems that support them. To achieve all this, it is essential to know which processes, technologies, and people are essential for the stability of the organization.
2. Scenario preparation and development
First, the Red Team services should meet with the IT provider to jointly analyze the results of the TTI. Based on the results of this report, the different scenarios to be developed will be evaluated.
The Red Team will design an action plan based on all the information analyzed. This document will contain the proposed scenarios to be carried out, as well as the controls to be applied to ensure that the test is carried out in a controlled manner.
This plan will also establish the objectives of the scenarios (the flags to be captured), as well as the tactics, techniques, and procedures (TTPs) to be simulated in order to achieve them.
3. Execution of the developed plans
This is undoubtedly the most delicate phase of the tests included in the TIBER-EU framework for Red Team teams: the execution of the attack scenarios. It should be noted that the use of the same tools used by attackers in real scenarios is key to this work.
This is because it makes it possible to complement detection capabilities at all points in the chain, measuring effectiveness in each of the phases into which the execution of the plans is divided:
- Reconnaissance phase. The attack surface is monitored, fingerprinting and active reconnaissance of accessible assets are performed.
- Intrusion phase. Identified weaknesses are exploited to obtain the first level of compromise.
- Lateral displacement/escalation. The assets necessary to achieve the defined objective are compromised, as well as the elevation of privileges sufficient to achieve it.
- Persistence. Activities are performed to maintain control of the compromised assets.
Each and every one of these actions must be documented by the Red Team services for follow-up and analysis.
Execution of offensive activities
The execution of attacks is the keystone of the Red Team’s work in the development of tests under a TIBER-EU scheme. The objective is to simulate attack scenarios in which the tactics, techniques, and procedures (TTPs) that are used in real cyber-incidents are captured.
All the information obtained by the Red Team is used to implement the necessary improvements to guarantee the protection of the financial institution’s system.
The attacks that are raised in a Red Team action plan are multiple, in order to cover all areas of the business and explore the banks or monetary authority’s system exhaustively. Among them we can highlight:
- Attacks against corporate applications, such as remote access or company websites.
- Physical attacks against corporate devices that connect to wireless networks.
- Brute force attacks against users and authentication platforms.
- Attacks against transactional infrastructure and platform software components.
- Attacks against cloud infrastructure and microservices.
- Attacks against communications devices.
- Evasion of WAF and perimeter security elements.
- Sending targeted attack campaigns through spear-phishing or phone calls directed against company employees.
- Creation and distribution of APTs physically or through online means to penetrate user equipment.
- Attempts to gain physical access to network points.
- Attacks against exposed communications devices, such as WiFi networks.
Once all these exercises have been executed, it will be time to complete the closing phase. This stage will focus on knowledge sharing and testing. The Blue Team teams of the financial institution will analyze the reports produced by the Red Team services after having done their work.
Subsequently, Purple Team tests will be carried out based on the improvements introduced by the Blue Team in the bank’s systems. And the effectiveness of this performance will be measured. In other words, wether the bank will be more and better prepared to face the growing number of cyber threats.
This operation will provide «360 feedback» on both the Red Team’s behavior and the cybersecurity structures in place at the banks.
This is the TIBER-EU framework. The time to shield financial institutions.
Discover our work and cybersecurity services at www.tarlogic.com
This article is part of a series of articles about TIBER-DORA-NIS2
- TIBER-EU, time to close the cybersecurity overdraft
- TIBER-EU calls on cyber intelligence to arm banks
- Red Team, the soldiers of the TIBER-EU program
- DORA Regulation: Can your bank withstand a cyber-attack?
- NIS2: Strengthening the cybersecurity of the EU’s strategic sectors
- Dear CEO: Ignoring cybersecurity will cost you dearly
- TLPT tests: What are they and which companies should perform them?
- When will the NIS2 directive be implemented in Spain?