Fancy Bear and where to find them
Table of Contents
Spain has been targeted by several APT (Advanced Persistent Threat) recently [1], amongst which we can find APT-28, also known as Fancy Bear. This group has many different names, depending on the researched referring to them. Some of those names are: Sofacy, Group 74, Pawn Storm, Sednit and Strontium. Here we will refer to this group as Fancy Bear.
Who is Fancy Bear?
Fancy Bear is a Russian APT group, which is supposedly related to the GRU (Russian Chief Intelligence Office). They started acting between 2004 and 2004 and their main goal is espionage and information theft. They are specially interested in information that could be useful for the Russian government. Because of this, they normally target sector related to critical infrastructures such as: governments, media, oil and gas or defense. With respect to their target countries, they have attacked several different ones. Nevertheless, they are usually focused on the NATO (North Atlantic Treaty Organization) member countries.
APTs are characterized by being highly specialized in their victims. With regard to Fancy Bear, they have been seen exploiting vulnerabilities in the past related to Microsoft, Adobe, Internet Explorer and Oracle. All of that technologies have something in common: they are largely used in their victims’ environments.
So, Fancy Bear focuses on emerging vulnerabilities which could give them access to their targets. In fact, it has been recently discovered that this group has actively exploited an Outlook vulnerability (CVE-2023-23397) that allowed them to steal NTLM hashes, which were later on used for moving laterally in the victim networks [2].
Malware and TTPs
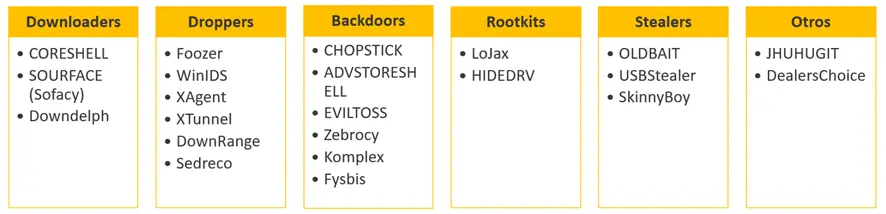
Each APT group is characterized by a particular set of Tactics, Techniques and Procedures (TTPS), as well as specific malware and tools. Regarding Fancy Bear, they have been found to use the following malware:
Moreover, they are known to use certain techniques for each one of their attack’s phases.
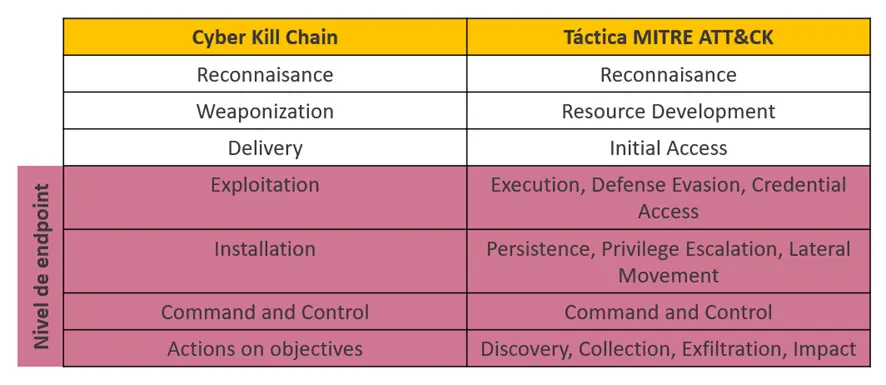
We have made an study of those TTPs, based on the Threat Hunting point of view. We normally use EDR/XDR technology for our investigations. This technology collects all the endpoint related information from the system. Endpoints are the main target of APTs so, with this approach, we are able to focus our searches on the more vulnerable machines.
Nevertheless, we lose visibility of the first phases of an attack:
Therefore, this study is focused on the last four steps of the Cyber Kill Chain. It is important to emphasize that there exist some EDR/XDR technologies which have visibility of the Delivery phase (Initial Access in MITRE ATT&CK framework).
However, there are huge differences in this respect among the vendors, and not all Initial Access’ techniques are visible from EDR/XDR tools. Because of this, Fancy Bear’s initial access techniques have not been investigated. Just for information, in the majority of their attacks they have used phishing for initial access (T1566).
Developed queries
The following queries have been designed to be executed in an EDR/XDR. All of them are written in pseudocode, as to be completely agnostic to the EDR technology used and to make reading easier.
Below you can find the techniques used by Fancy Bear for each one of the aforementioned tactics and a possible query to detect that behavior on an EDR/XDR.
TA0002: Execution
– PowerShell usage to download scripts or second-stage malware (T1059.001).
For doing this, different PowerShell cmdlets can be used. In order to detect them, we can look for these cmdlets in the command line:
process = “powershell.exe” and command_line in contains (“DownloadFile”, “Invoke-WebRequest”, “DownloadString”, “iwr”)
– Manually execution of LNK file by the user (T1204.001).
There are some EDR/XDR which have specific events to detect the execution of LNK files. For those that do not have that event, we can do the following approach: look for the opening of a LNK by the file explorer (explorer.exe) and, just after that, the execution of a suspicious process.
In this query, we have identified some processes that allow the execution of code. Another option would be to look for the execution of non-signed processes.
event_type = FILE_OPENED and parent_process = “explorer.exe” and extension = “lnk”
| join (event_type = PROCESS and process in (“cmd.exe”, “powershell.exe”, “wscript.exe”, “mshta.exe”)) by endpoint_id, process_id
| where time_difference (t1, t2) < 5 seg
TA0003: Persistence
– Logon scripts usage (T1037.001).
Fancy Bear has been seen including scripts in the registry key HKCU\Environment\UserInitMprLogonScript. Any script stored in that registry key would be executed each time that user (current user) logs in.
– Startup folder usage (T1547.001).
They use the Startup folder in order to obtain persistence in the system. There are two different Startup folders. If the folder C:\Users\[Username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup is used, the malware will be executed when the user [Username] logs in. On the other hand, if C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp is used, it will be executed each time a user logs in (no matter which one, it is executed for every user).
event_type = FILE_CREATED
and file_path regex “(?i)^(C:\\Users\\.*\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\|C:\\ProgramData\\Microsoft\\Windows\\Start Menu\\Programs\\StartUp).*”
and file_name != “desktop.ini”
– “Office Test” registry key usage (T1137.002).
This group has used the registry keys HKEY_CURRENT_USER\Software\Microsoft\Office test\Special\Perf or HKEY_LOCAL_MACHINE\Software\Microsoft\Office test\Special\Perf to store malicious DLLs which would be executed each time a Microsoft Office application is started. These registry keys are not created by default, they must be manually created.
event_type in (REGISTRY_CREATE_KEY, REGISTRY_SET_VALUE) and registry_key contains “\Software\Microsoft\Office test\Special\Perf”
TA0004: Privilege Escalation
In what refers to privilege escalation, Fancy Bear normally exploits emerging vulnerabilities on widely used software. In their attacks, they have exploited the following ones: CVE-2014-4076, CVE-2015-2387, CVE-2015-1701 y CVE-2017-0263, among others.
Nevertheless, designing specific queries for detecting those vulnerabilities is nor really our goal in Threat Hunting. Preventing the exploitation of existing vulnerabilities would be the task of a vulnerability management department. Furthermore, these vulnerabilities will change with time, as old ones would be patched, and new ones would be discovered. Therefore, it does not really make sense to limit our searches to the vulnerabilities exploited in previous attacks.
Because of this, we have decided to make the following approach: making a query that detects the usage of legitimate Microsoft’s binaries commonly used for bypassing UAC (User Account Control).
– Commonly used binaries for bypassing UAC spawning child processes with elevated privileges (T1548.002).
event_type = PROCESS_START
and parent_process in (“WSReset.exe”, “slui.exe”, “fodhelper.exe”, “eventvwr.exe”, “cmstp.exe”, “sethc.exe”)
and child_process_integrity_level in (“High”, “System”)
TA0005: Defense Evasion
– Decoding Base64 payload with certutil (T1140).
Fancy Bear has been seen coding its payloads in Base64 and storing them in TXT files. Later on, so as to execute those payloads, they decode them using certutil -decode.
process = “certutil.exe” and command_line regex “(?i).*\-decode.*\.txt.*”
– Clearing event registries with wevtutil (T1070.001).
They clear event registries by using the command wevtutil cl. More precisely, they normally clear the Security and System event registries. We have decided to add to our query the Application event registry, as it is another one that is commonly cleared by adversaries.
command_line regex “(?i).*wevtutil\s+cl\s+(system|security|application).*”
– Execution of malicious DLLs with rundll32 (T1218.011).
This group commonly stores the malicious DLLs in C:\Windows\ or in C:\Users\[Username]\AppData\. Later on, they execute does DLLs with rundll32.
command_line regex “(?i).*rundll32\.exe.*(C:\\Windows|C:\\Users\\[\w\s\.]+\\AppData|[A-Z]:)\\[\w\s\.]+\.dll.*”
TA0006: Credential Access
– LSASS dump with rundll32 (T1003.001).
The function Minidump from comsvcs.dll is widely used for dumping process memory. If they dump lsass.exe process memory, they are able to access the hashes of the users’ credentials.
process = “rundll32.exe” and command_line regex “(?i).*comsvcs\.dll, MiniDump.*”
– Dumping SAM database (T1003.002).
It is possible to dump SAM (Security Account Manager) database by using reg.exe save. This Will allow attackers to obtain the users’ credentials hashes. Furthermore, SAM database is encrypted with the SysKey, that can be obtained by dumping the SYSTEM registry hive. On the other hand, the SECURITY registry hive is also interesting, as it contains LSA secrets. Therefore, with this query we look for the dumping of any of these registry hives:
process = “reg.exe” and command_line regex “(?i).* .*save.*(hklm|HKEY_LOCAL_MACHINE)\\(sam|security|system).*”
– Dumping NTDS.dit (T1003.003).
The file C:\Windows\NTDS\Ntds.dit is located in domain controllers and it contains important information regarding Active Directory, including the users’ credentials. Fancy Bear has been seen using ntdsutil.exe to export the data from this file.
process = “reg.exe” and command_line regex “(?i).* .*save.*(hklm|HKEY_LOCAL_MACHINE)\\(sam|security|system).*”
TA0007: Discovery
– Using forfiles to locate PDF, Excel or Word files (T1083).
The command forfiles may be used to look for certain files on a system, based on a given pattern. Fancy Bear uses this tool to look for PDF, Word and Excel files that may contain interesting information (so as to export that information later on).
process = “forfiles.exe” and command_line regex “(?i).*\.(xls|xlsx|doc|docx|pdf|ppt|pptx).*”
– Reading files from folders with sensitive information (T1083, T1518).
This query was designed based on the behavior of the stealer SkinnyBoy, which is a common malware used by this group. This stealer opens files from several different folders. Therefore, we look for non-signed processes which open more than 5 of those sensitive subfolders. This behavior is typical from any stealer, so this query could also be used to detect other stealers.
event_type = FILE_OPENED
and parent_process is not signed
and file_path REGEX “(?i)^(C:\\Users\\.*\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Administrative Tools\\|C:\\Users\\.*\\AppData\\Roaming\\|C:\\Users\\.*\\AppData\\Roaming\\Microsoft\\Windows\\Templates\\|C:\\Users\\.*\\AppData\\Local\\Programs\\|C:\\Program Files( \(x86\))?\\)([a-zA-Z0-9\-\._]+)\\.*”
| set folder = regextract(file_path,”(?i)^(C:\\Users\\.*\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Administrative Tools\\[a-zA-Z0-9\-\._]+\\|C:\\Users\\.*\\AppData\\Roaming\\[a-zA-Z0-9\-\._]+\\|C:\\Users\\.*\\AppData\\Roaming\\Microsoft\\Windows\\Templates\\[a-zA-Z0-9\-\._]+\\|C:\\Users\\.*\\AppData\\Local\\Programs\\[a-zA-Z0-9\-\._]+\\|C:\\Program Files\\[a-zA-Z0-9\-\._]+|C:\\Program Files \(x86\)\\[a-zA-Z0-9\-\._]+)\\.*”),1)
| counter = count_distinct(folder) by host, parent_process_pid
| where counter > 5
TA0008: Lateral Movement
– Sending malicious files through SMB (T1548.002).
They use SMB to send malware through the whole network. This allows them to move laterally inside it. Remember that the commonly used ports for SMB are 445 and 139. Therefore, we can look for the creation of suspicious files sent through any of those two ports:
event_type = NETWORK_INBOUND and local_port in (445,139)
| join (event_type = FILE_CREATED and file_extension in (“exe”, “dll”, “bat”, “vbs”) by endpoint_id
| where time_difference (t1, t2) < 5seg
– Using net to map network drives (T1021.002).
Fancy Bear has used administrator credentials to map network drives. For doing this, they have used commands similar to: net use [A-Z]: \\{network_drive}
process in (“net.exe”, “net1.exe”) and command_line regex “(?i).*net.*use.*[A-Z]:.*\\\\.*”
TA0009: Collection
– Making screenshots in the victim machine (T1113).
With the goal of stealing sensitive information, once they have gained access to the target system, they make screenshots of the victim’s screen.
There are various tools that can be used for doing this. Two of them are PowerShell and NirCmd. Based on this premise, the following query has been designed:
event_type = FILE_CREATED and parent_process in (“powershell.exe”, “nircmd.exe”) and file_path regex “.*\.(png|jpeg|jpg|svg|bmp)$”
– Store stolen information in a TMP file in %ALLUSERSPROFILE% (T1074.001).
Fancy Bear stores all the stolen information from the victim in a temporal file in C:\ProgramData\. Later on, they exfiltrate that information.
event_type = FILE_CREATED and file_path regex “(?i)^C:\\ProgramData\\[\w\s\_]+\.tmp$”
TA0010: Exfiltration
– Dividing files in fragments of less than 1MB (T1030).
Before exfiltration, Fancy Bear divides the files with the collected information in fragments of less than 1MB.
event_type = FILE_CREATED and file_path regex “(?i)^[A-Z]:(\\Windows\\|\\Users\\[\w\s\.]+\\AppData\\|\\ProgramData\\|\\)[\w\s\.\_]+\.\w+” and file_size < 1MB
| count as created_files by parent_pid, endpoint_id
| where created files > 5
– Data exfiltration using Google Drive (T1567.002).
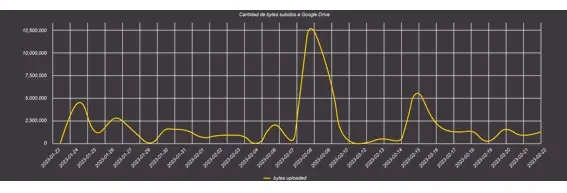
Fancy Bear has been seen using Google Drive as cloud storage to which they send the collected information. To detect this exfiltration, we may focus our investigation on a volumetric study. In this case we should look for deviations with respect to the normal pattern from our company.
The following query allows us to generate a line graph representing the number of bytes sent to Google Drive each day for one month. If we find a day in which these number of bytes increases significantly, it may indicate an exfiltration attempt.
event_type = NETWORK_CONNECTION and URL contains any (“drive.google.com”, “www.googleapis.com”)
| sum (bytes_uploaded) by date
TA0011: Command and Control
– Using Google Drive as Command and Control server (C2) (T1102.002).
In order to execute command on the victim machines (sent from the C2 server), they use the Google Drive API. Each 20 minutes, the malware installed in the victim looks for files named cmd_{victim_ID} in a certain Google Drive folder. These files contain the commands to be executed [3]. With this query we look for connections to this API from suspicious processes:
event_type = NETWORK_CONNECTION
and URL contains “www.googleapis.com/upload/drive”
and parent_process not in (“msedge.exe”, “chrome.exe”, “firefox.exe”, “opera.exe”, “iexplore.exe”, “GoogleUpdate.exe”, “OUTLOOK.EXE”)
This post is a summary of the talk Fancy Bears and Where To Find Them, given by Ana Junquera Méndez in RootedCON 2023.
References
[1] SOCRadar, “Spain: Threat Landscape Report,” 2022.
[2] S. Gatlan, “Microsoft fixes Outlook zero-day used by Russian hackers since April 2022,” 2023. [Online]. Available: https://www.bleepingcomputer.com/news/microsoft/microsoft-fixes-outlook-zero-day-used-by-russian-hackers-since-april-2022/. [Accessed 20 marzo 2023].
[3] F. Hacquebord and A. Remorin, “Pawn Storm’s Lack of Sophistication as a Strategy,” 2020. [Online]. Available: https://www.trendmicro.com/en_us/research/20/l/pawn-storm-lack-of-sophistication-as-a-strategy.html. [Accessed 21 marzo 2023].
[4] NSA, CISA, FBI, & NCSC, “Russian GRU Conducting Global Brute Force Campaign to Compromise Enterprise and Cloud Environments,” 2021.
[5] FireEye, “APT28: A window into Russia’s cyber espionage operations,” 2014.
[6] FireEye, “APT28: At the center of the storm,” 2017.
[7] Perception Point, “Incident Report: AP28 – Fancy Bear,” 2019. [Online]. Available: https://perception-point.io/blog/incident-report-ap28-fancy-bear/. [Accessed 20 marzo 2023].
[8] R. Falcone, “Technical Walkthrough: Office Test Persistence Method Used In Recent Sofacy Attacks,” 2016. [Online]. Available: https://unit42.paloaltonetworks.com/unit42-technical-walkthrough-office-test-persistence-method-used-in-recent-sofacy-attacks/. [Accessed 20 marzo 2023].
[9] CyberMasterV, “A Step-By-Step Analysis Of The New Malware Used By APT28/Sofacy Called SkinnyBoy,” 2021. [Online]. Available: https://cybergeeks.tech/skinnyboy-apt28/. [Accessed 20 marzo 2023].
[10] Crowdstrike, “Who is FANCY BEAR (APT28)?,” 2019. [Online]. Available: https://www.crowdstrike.com/blog/who-is-fancy-bear/. [Accessed 20 marzo 2023].
[11] ESET Research, “Sednit update: Analysis of Zebrocy,” 2018. [Online]. Available: https://www.welivesecurity.com/2018/04/24/sednit-update-analysis-zebrocy/. [Accessed 20 marzo 2023].
[12] ESET Research, “LoJax: primer rootkit de UEFI en uso que se descubre, cortesía del grupo Sednit,” 2018. [Online]. Available: https://www.welivesecurity.com/la-es/2018/09/27/lojax-primer-rootkit-uefi-en-uso-cortesia-grupo-sednit/. [Accessed 20 marzo 2023].