DSL Communications Interception – Administration – part 3
We continue with the articles on ADSL router security analysis and communications interception (See Part I and Part II).
One of the most interesting elements to analyze in a DSL infrastructure is the Administration traffic that is generated against and from our DSL device. Currently all DSL routers or cablemodems provided by an ISP can be managed and administered remotely.
The administration traffic is generated from the WAN, so it is not possible to analyze it without an ATM sniffer or, as in our case, our own DSL infrastructure with a DSLAM.
Several particularly relevant elements are involved in remote management and administration:
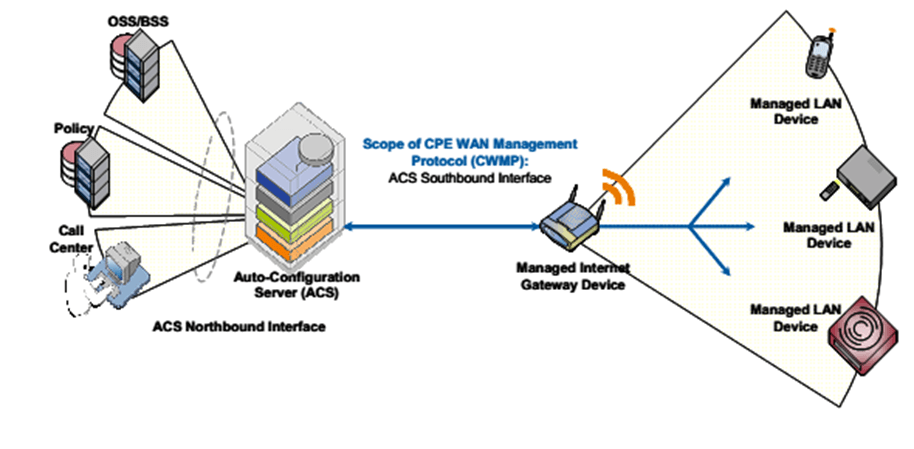
- TR-069: This is a protocol for remotely configuring and administering client routers, also called CPE (Custom Premise Equipment).
- ACS: stands for “Auto configuration server” and is the ISP’s system in charge of managing the CPEs.
- CWMP: Acronym for “CPE WAN Management Protocol”, i.e. TR-069.
TR-069 also enables the management of devices behind the ADSL router.
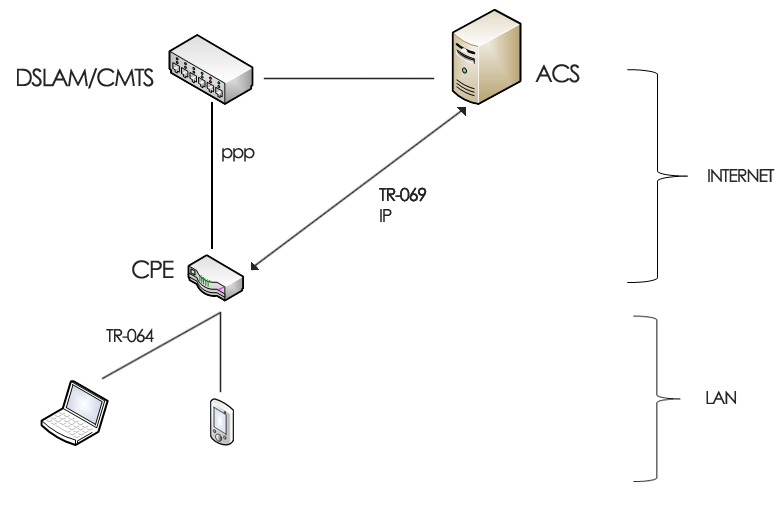
The following diagram illustrates how the CPEs and ACSs are connected. As can be seen there is another protocol in the LAN side called TR-064. This protocol and its security implications will be discussed in another article.
ACS access is usually restricted, for security reasons, from the IP address assigned to the ISP. For this reason, to perform the analysis of administration protocols it is necessary to have an IP address in the operator’s network range.
The solution used by our cybersecurity team in the lab was to generate VPN tunnels against systems located in network segments of several ISPs and route all incoming and outgoing traffic through that tunnel with the help of iptables. The router at the other end of the VPN tunnel must be in bridge mode or manually forward all ports into the tunnel.
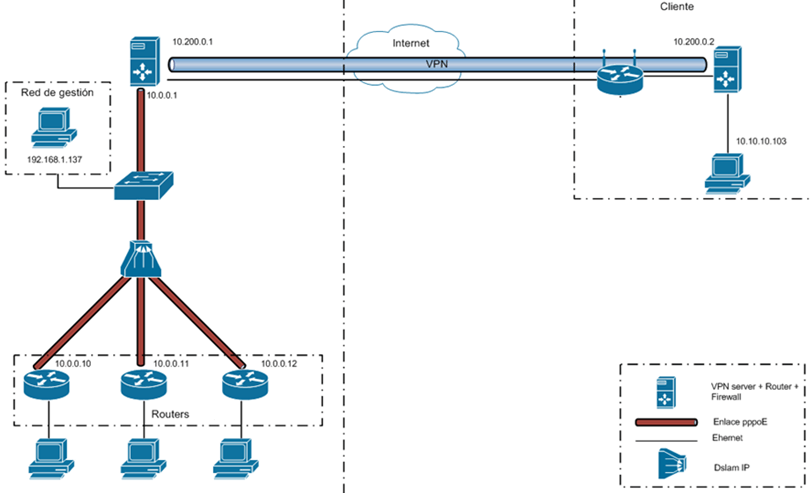
This last step can be omitted when our Internet connection is with the same provider as the router we want to analyze.
At this point we can begin the process of analyzing this administration related traffic.
Discover our work and cybersecurity services at www.tarlogic.com
This article is part of a series of articles about DSL Communications eavesdropping
- DSL Communications Interception – Introduction – Part 1
- Interception of DSL Communications – Synchronization – Part 2
- DSL Communications Interception – Administration – part 3
- DSL Communications Interception – TR069 – Part 4
