
TARLOGIC's BLOG
Cybersecurity - Page 6
Cybersecurity articles with security analysis and ethical hacking technics information

BlueTrust, goodbye to Bluetooth privacy
BlueTrust is the name of a new technique developed by Tarlogic that makes it possible to discover trust relationships between Bluetooth devices to obtain data of interest about the[...]
Read more
IoT Security assessment
Discover the IoT security assessment with best practice guides on each of the different stages of an IoT security audir that we have discussed in previous OWASP FSTM methodology ar[...]
Read more
OWASP FSTM, Stage 9: Exploitation of executables
Exploitation of executables is the final step in a firmware analysis, in which an exploit is developed for a vulnerability discovered in earlier phases Vulnerability exploitation o[...]
Read more
OWASP FSTM, step 8: Runtime analysis
Static analysis of the firmware and its executables provides only a limited amount of information about its operation and performing further analysis at that stage is inefficient i[...]
Read more
OWASP FSTM, step 7: Dynamic analysis
The dynamic analysis phase is defined as the study of the running device in a real or emulated environment. For this purpose, the device is analyzed, trying to delve into possible [...]
Read more
OWASP FSTM step 6: firmware emulation
Step 6 of the OWASP FSTM methodology shows how to perform firmware emulation of a device and builds on the previous steps[...]
Read more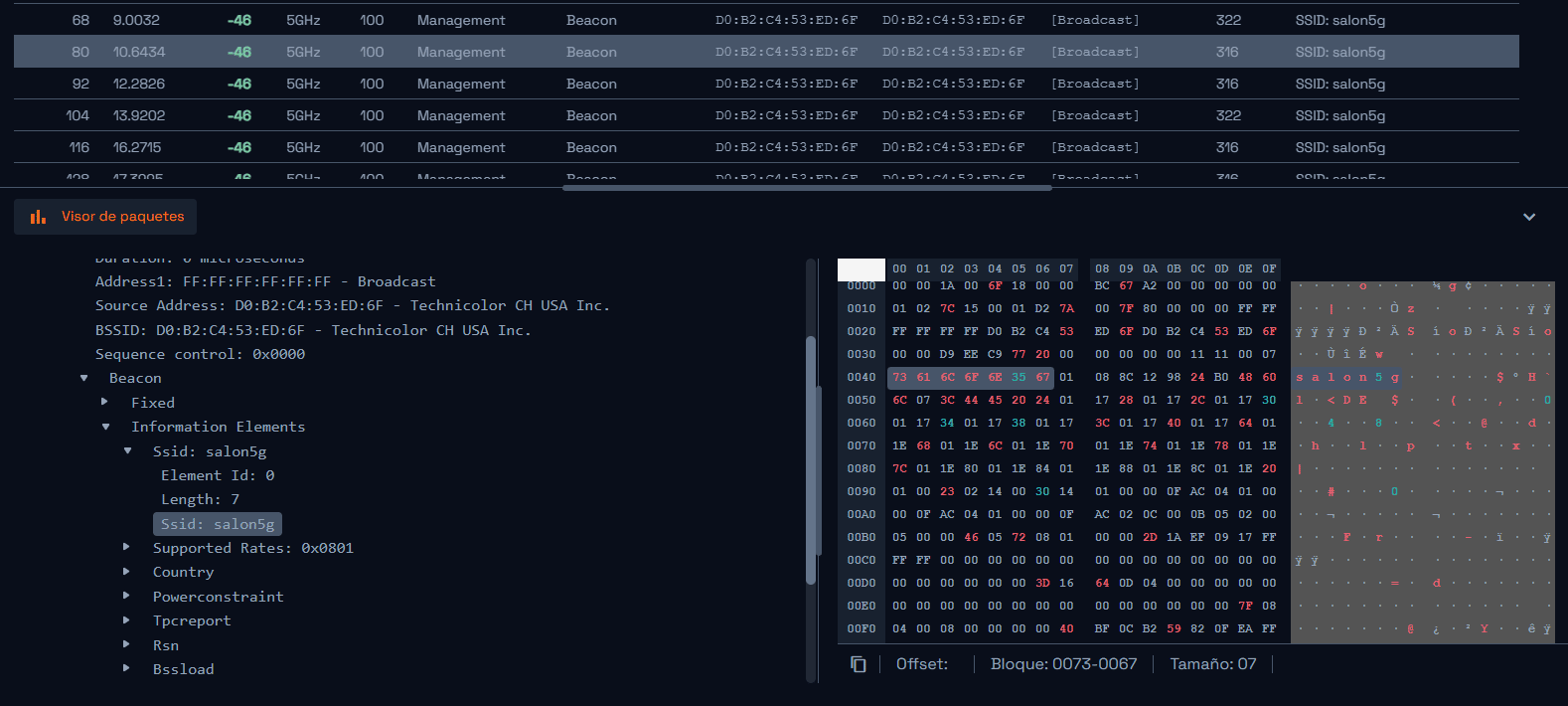
Wi-Fi Sniffer for Windows and 802.11 packet viewer
Acrylic Suite is a software developed by Tarlogic team that provides a powerful WiFi sniffer to analyse communications and WiFi security on Windows 11 and Windows 10 computers. To [...]
Read more
CVE-2022-42889: Text4Shell, Critical Vulnerability in Apache Commons Text
As happened in December last year with Log4Shell, the vulnerability that affected a multitude of Java products that made use of the Log4J library, a new alert has arisen for the vu[...]
Read more
OWASP FSTM, stage 5: Analyzing filesystem contents
The operation of IoT and embedded devices relies on an operating system that stores configuration and executable files in a file system embedded in the firmware. This article focus[...]
Read more
Google messes up: Office 365 login portal is not from Microsoft
«Office 365 login» With those words, many people start their workday to authenticate to Microsoft’s web tools, with which their companies are integrated. This Google search[...]
Read more